
How to Secure Workloads in Hybrid Clouds
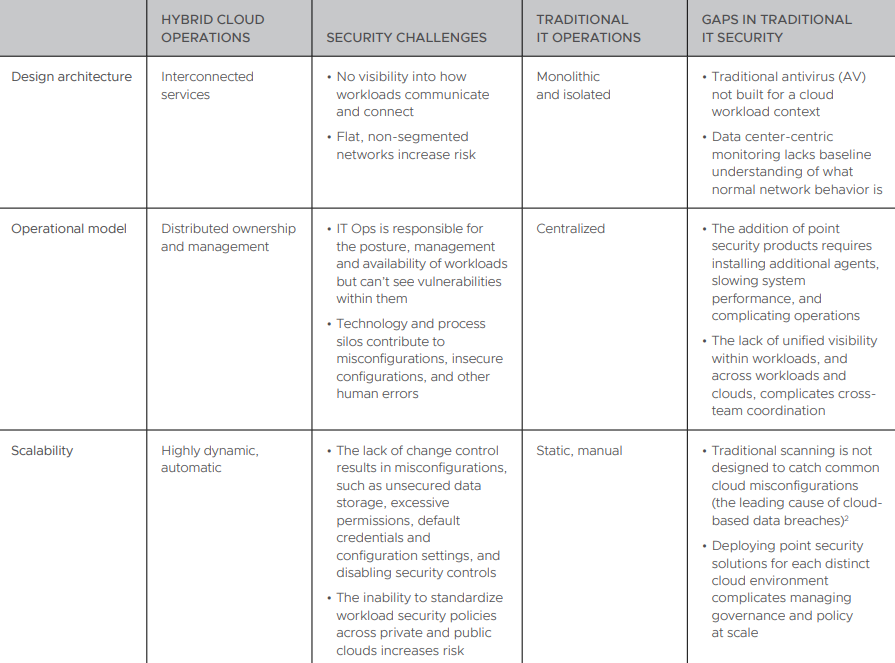
The hybrid cloud is at the centerpiece of digital transformation. Today, more than 90 percent of enterprises report using a multi-cloud strategy, with most combining their use of public and private clouds. The good news is that this approach offers the necessary flexibility and scalability to support rapid innovation. The downside is that it often adds increased complexity and risk, making security an essential component across private and public clouds.
As enterprise teams deploy and manage critical workloads across multi-cloud environments, visibility into the security posture of workloads and controlling the attack surface are critical for securing data and maintaining operations.
Many distinct teams across the enterprise, including IT Ops and SecOps, are key stakeholders in the performance, availability and security of cloud workloads. Keeping team members aligned rather than fragmented is also an essential success factor.
Security Challenges with Private, Public and Hybrid Clouds
Deploying and managing workloads and apps in private, public and hybrid clouds takes a village. What we once considered traditional IT has been replaced by a collective. IT Ops, DevOps and SecOps now team together to deliver and secure apps and services from the cloud.
Three Steps for Redefining Risk
The best way to make the most of digital transformation is to accept how much of a paradigm shift it represents. Old risk management models no longer apply when change is a constant and there are so many cooks in the kitchen.
When securing cloud workloads, enterprise teams need to:
- Increase visibility – Identify unknown or undetected risks in workloads.
- Speed recovery – Accelerate risk recovery by building resilience into cloud workloads.
- Simplify security – Unify risk mitigation across workloads, endpoints and containers.
Intrinsic Security for Cloud Workloads
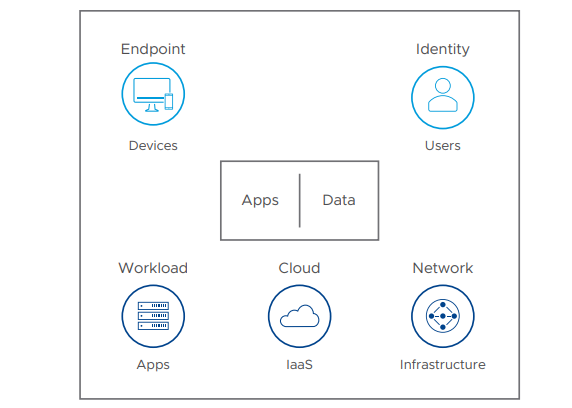
With the VMware intrinsic security approach, deep monitoring and behavioral analysis are implemented at each control point: cloud, workload, endpoint, network and identity, and then unified for full contextual awareness. Like a video camera that records each move at every control point, intrinsic security enables comprehensive contextual awareness. Because there’s no need to manually stitch together telemetry from disparate control points, teams can quickly track down threats from the point of entry and every step in between.
VMware Cloud Workload Protection: How It Works
The VMware intrinsic security approach enables enterprises to protect cloud workloads by utilizing existing infrastructure to proactively identify risks, prevent exploits and exposures, and quickly detect and respond to new and emerging threats.
The three-step process works in the following way, supported by essential security controls.
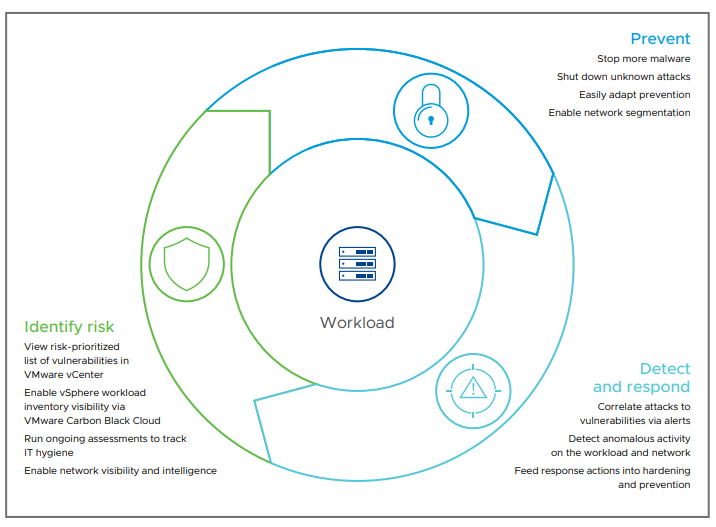
Step One: Identify risk
- Initial state integrity check – VMware Carbon Black Cloud conducts an initial state integrity check to validate the system you’re installing the workload on is clean, compliant and appropriate for the type of workload. It will also collect and analyze OS patch levels, assess vulnerabilities and misconfigurations, and determine if additional hardening is required.
- Ongoing visibility into system state – VMware Carbon Black Cloud identifies configuration drift, the presence of unknown or unauthorized applications, vulnerabilities, and other dynamic activity that increases the environment’s attack surface. For example, it will:
– Monitor for any changes that indicate nefarious activity (e.g., zeroing out passwords, changes in BitLocker configuration)
– Audit and remediate to query 1,500 artifacts for each workload and endpoint across private and public clouds
– Empower admins to run custom SQL queries to look out for specific malicious behavior or activity - Ongoing visibility into vulnerabilities and network activity – VMware Carbon Black Cloud enables vSphere admins to view risk-prioritized workload vulnerabilities in VMware vCenter® and regularly run scan-free vulnerability assessments across workloads. NSX delivers a built-in distributed firewall, so IT Ops teams can monitor communication of workloads across private and public clouds, determine which workloads are part of an app, and determine how to segment unrelated workloads.
Step Two: Prevent risks from escalating
- Prevent exploits on the workload – VMware Carbon Black Cloud delivers next-generation antivirus (NGAV) for protection that transcends point-in-time indicators for malware, ransomware, zero-day, rapid variants, suspicious files, and potentially unwanted processes (PUPs) specific to workloads across private and public clouds. The VMware platform combines ransomware decoys, dynamic analysis, and machine learning to provide ongoing analysis that prevents suspicious files from executing.
- Prevent non-malware attacks – In addition to blocking malware attacks, VMware Carbon Black Cloud protects against the latest persistent attacks using fileless malware, memory-based, and living-off-the-land (LotL) tactics. These pernicious attacks use existing software and allow listed apps (e.g., PowerShell), and authorized protocols to carry out malicious activities. Unlike legacy approaches that rely on known threats, the VMware platform can identify new variants and zero-day exploits by piecing together connected behaviors.
- Prevent network-based attacks – The NSX Service-defined Firewall protects workloads by mitigating lateral movement and blocking inbound exploits of vulnerable apps and services. With this level of visibility, you can understand how LotL attacks move across the network, identify indicators of compromise (IOCs), and lock down these network connections to isolate workloads from attackers.
- Customize prevention – Every environment has different and often competing operational constraints. VMware offers our customers the ability to balance security and operational risks with precise granularity. With the VMware policy engine, you can choose how to mitigate threats based on the specific type of workload, its function, criticality, and adjacency to other critical workloads. For example, to isolate a mission-critical workload, a sysadmin can prevent PowerShell from scraping the memory of another process or invoking an untrusted application.
Step Three: Detect and respond to ongoing risks
- Know when and where to start an investigation (zoom in) – Use VMware out-of-the-box automated threat detection via updated threat intelligence from the VMware Threat Analysis Unit™ to pinpoint affected systems and isolate them for remediation. VMware APIs allow you to integrate your own third-party feeds and watch lists, and round out collaborative threat sharing information from VMware’s robust user exchange.
- See the full scope and time frame of the attack (zoom out) – The VMware platform allows investigators to rewind the tape to understand how an attack unfolded, which systems were affected, and how the attack progressed over time. Because VMware captures all the data (e.g., detailed process activity, process-to-process interaction, parent-child process relationships, etc.), building a detailed timeline without blind spots—well after the fact—empowers incident response and forensic teams to get to the truth.
- Rapid detect-to-prevent workflow – In three easy steps, VMware Carbon Black Cloud enables you to translate threat detection into standardized prevention policy across your workloads. First, apply automated policies based on previous detections customized for your workloads. Second, instantly preview the downstream effects of the prevention policy before it’s implemented. Third, with a single click, roll out the updated policy across workloads on any environment.

