Security That Overcomes Today’s Challenges
CISOs and their security teams face a growing number of challenges in trying to protect against successful cyberattacks:
- The new battleground for cyberthreats is inside the data center
- Teams have little to no visibility into east-west traffic
- Threats that make it past the perimeter can move laterally over allowed data center traffic with little to block them
- Work-from-home models and virtual desktop infrastructure (VDI) allow traffic straight into the data center, exposing the workloads running within to threats
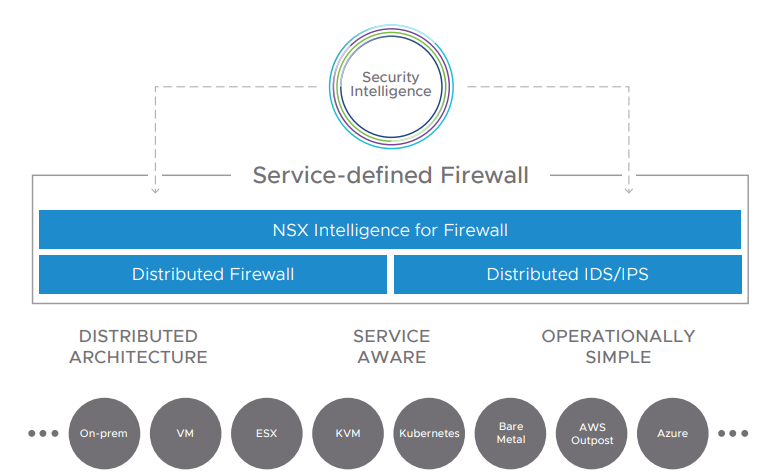
Traditional appliance-based security solutions are ineffective at providing visibility into all east-west traffic, protecting that traffic, and preventing the lateral movement of threats. That’s why enterprises are turning to VMware’s Service-defined Firewall, a distributed internal firewall that protects all east-west traffic with security that’s intrinsic to the infrastructure, thereby radically simplifying the deployment model. (To learn more about the challenges of traditional network security controls for protecting modern workloads, read the white paper Five Critical Requirements for Internal Firewalling in the Data Center.) With the Service-defined Firewall, security teams can protect the brand from internal threats and minimize the damage from cyberattacks that make it past the traditional network perimeter. The solution includes a distributed firewall, an intrusion detection and prevention system (IDS/IPS), and analytics through NSX Intelligence.
Implementing any new security approach or solution requires time and commitment from a security team already stretched thin. For that reason, although implementing east-west security is easier and faster with a distributed internal firewall, most organizations will still prefer to take an iterative, phased approach to improving data center security.
In addition to not overwhelming the team with a major initiative, breaking the deployment of an internal firewall into smaller projects delivers other benefits as well: It lets security teams prove success early and demonstrate the value of the approach to internal stakeholders. They can then choose to build on their experience to expand the use of distributed internal firewalling, gaining organizational maturity, speed, and confidence as they progress.
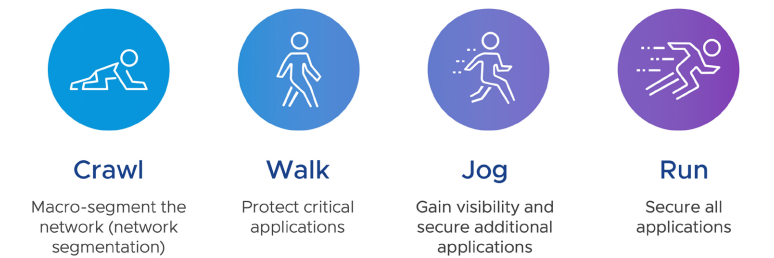
While there are different approaches, the following four steps (Figure 2) have been used by VMware customers to start small and then continually strengthen their data center defenses over time:
- Crawl: Macro-segment the network
- Walk: Protect critical applications
- Jog: Gain visibility and secure additional applications
- Run: Secure all applications
Crawl: Macro-Segment the Network
For many organizations, the first step in protecting east-west traffic is the most difficult. That’s because attempting to macro-segment the network using traditional, appliancebased firewalls has proven to be time-consuming, complex, and inflexible—as well as expensive.
However, using a distributed internal firewall simplifies security architecture and accelerates time-to-value, making it easier to deploy macro-segmentation to improve the security of east-west traffic. It’s also more flexible, adapting easily to changing network and security requirements as the business evolves.
With the Service-defined Firewall, your security team can start using network segmentation to isolate and secure specific environments, such as development and production, from each other. This immediately prevents attackers and malicious insiders from moving laterally between these environments.
Goal: Deploy the Service-defined Firewall to protect segments of the network by creating virtual security zones. By macro-segmenting these environments, the security team can improve the overall security stance for the data center by preventing lateral movement between zones.
Walk: Protect Critical Applications
Typically, the next step to securing the data center is to start moving from macrosegmentation to micro-segmentation, which enables the security team to define and enforce more granular controls, right down to the workload level.
The security team chooses a small number of well-understood applications that are critical to the business and should be isolated and protected with additional security controls to prevent unauthorized access, data breaches, and other forms of attack.
For these applications, the granular security controls can be further enhanced with IDS/IPS capabilities to detect traffic patterns that can indicate an attack. While isolating applications may be possible with some solutions that are expressly designed for microsegmentation, those solutions don’t provide IDS/IPS capabilities, which are required for compliance with regulations such as the Health Insurance Portability and Accountability Act (HIPAA) and the Payment Card Industry Data Security Standard (PCI DSS).
Goal : Use micro-segmentation to isolate and protect one or more critical applications, applying layered security controls specific to the application and preventing lateral movement by attackers either into or out of the segment where the application runs.
Jog: Gain Visibility and Secure Additional Applications
As the security team gains more experience in operating a distributed internal firewall, it can continue expanding its monitoring and protection of east-west traffic to additional critical or important workloads within the data center.
For applications that are not well-understood, the Service-defined Firewall gives the security team data center-wide visibility and applies built-in machine learning to help the team understand applications and traffic flows. Automated application discovery gives the security team a comprehensive map of application topography as well as automatically generated recommendations for security policies based on observed traffic flows.
Goal: Build on the knowledge and skills your team gained in the first two steps and use the built-in visibility and automation in the Service-defined Firewall to isolate and secure more workloads, which further reduces the attack surface and strengthens data center security.
Run: Secure All Applications
At this point in the journey, security teams are ready to secure all the applications in the data center using the Service-defined Firewall to further mitigate security risk, while easily scaling to protect new workloads and increased traffic. They can also enable compliance with regulatory requirements using the Service-Defined Firewall’s IDS/IPS capabilities. Organizations that previously used appliance-based perimeter firewalls as internal firewalls will reduce costs as they displace them with the Service-defined Firewall.
Goal: Extend the deployment of the Service-defined Firewall to inspect and protect all eastwest traffic in the data center and provide additional layers of protection for sensitive workloads using the firewall’s IDS/IPS capabilities.

