Check Point is a leader in security software solutions. Their products include threat prevention, mobile security, endpoint security, firewalls, and security management.
Check Point is a leader in security software solutions. Their products include threat prevention, mobile security, endpoint security, firewalls, and security management.
U.S. Headquarters: San Carlos, CA
Founded: 1993
Mission: “Check Point Software Technologies is the worldwide leader in securing the Internet. Making Internet communications and critical data secure, reliable and available everywhere has been and continues to be our ongoing vision. We are committed to staying focused on real customer needs and to developing new and innovative security solutions that redefine the security landscape.”
Check Point offers a full range of solutions to keep your data secure. One service they offer evaluates how secure your organization is through the Security Checkup. Your corporate network offers access to valuable and sensitive information that must never fall into the wrong hands. Are you sure there are no hidden “surprises” threatening your data assets, like malware, back doors or data leaks? Early exposure to hidden threats will enable you to immediately address these risks and enhance security. With Check Point, you can uncover these risks.
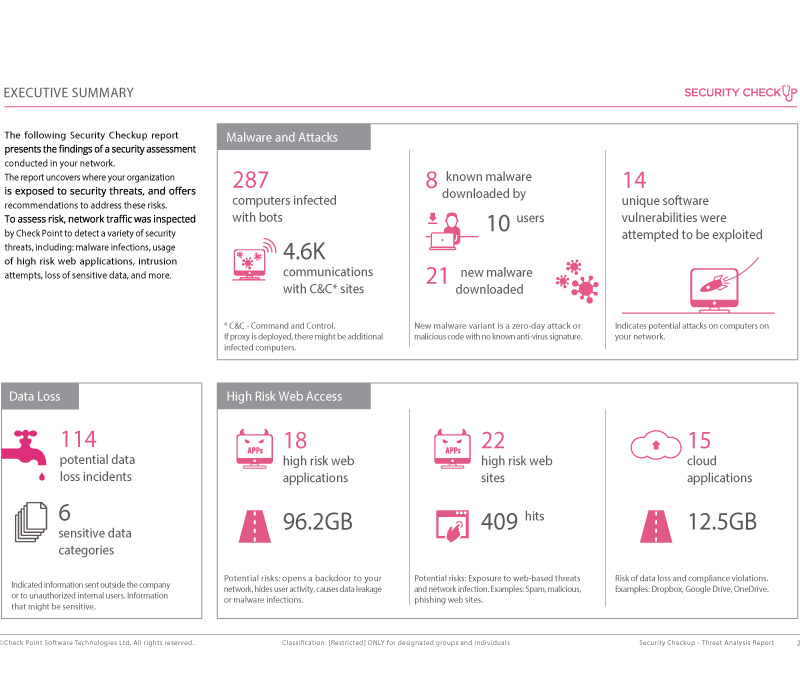
The Security Checkup is an assessment to identify risks in your organization. After the assessment you receive a full report with suggestions on how to better secure your organization.
Full Range of Security Risks
The report covers a full range of security risks:
- High risk web applications and websites used by employees such as: P2P File Sharing applications, Proxy anonymizers, File Storage applications, malicious websites, and more
- Analysis of malware threats including computers infected with bots, viruses, and unknown malware (zero day attacks and malware that cannot be detected by traditional anti-virus systems)
- Exploited vulnerabilities of servers and computers in the organization, indicating possible attacks
- Sensitive data sent outside the organization via emails or the web
- Bandwidth analysis identifying the top bandwidth consuming applications and accessed websites to understand who and what is hogging your network bandwidth
- For existing Check Point customers with active Security Management: Compliance and best practices comparing the current rule base configuration with Check Point best practices recommendations and also with many industry standards including PCI, HIPAA, ISO, and others